A few days ago, the CTF team I play with, Dc1ph3r, hosted our first ever CTF, InfernoCTF ( with prizes from pentesterlab :D ). I focused on making challenges for the OSINT category, and tried to make them relatively easy as a lot of the pwn/rev challenges were quite difficult and wanted to balance it out a bit :P
I know OSINT challenges get a bad reputation, but I promise these aren't guessy!
There are already many writeups available for these challenges (I'll link them below), which is awesome, but I wanted to provide the perspective of the author as that could be useful for some people.
New Developer: Easy
A friend of a friend of a friend who is known for leaking info was recently hired at a game company. What can you find in their GitHub profile?
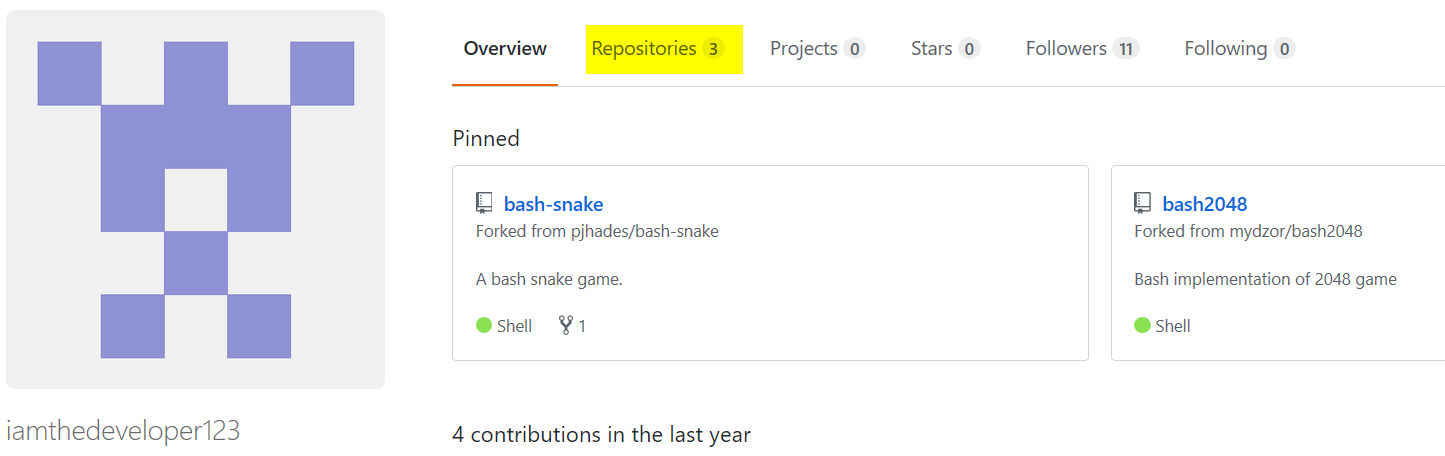
I'd also like to point out that this fake github profile has more followers than my actual github ;(
The goal of this challenge was to show the player that often times people leave things in their GitHub profiles that shouldn't be made public. A relatively commonly seen example of this is employees leaving aliases, keys or similar things in their dotfiles that could lead to security issues.
From quickly viewing the recent commits, you can see that the developer only made additions to bash2048 and dotfiles, so bash-snake can be ignored.
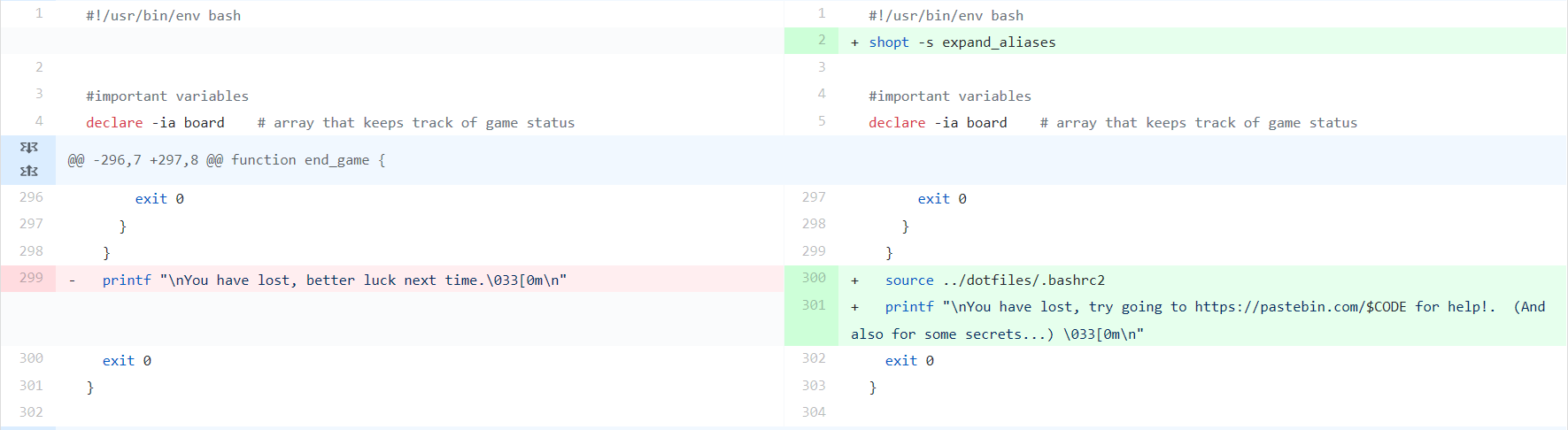
First, by looking at the commit to bash2048 you would have been able to see that the user used source on .bashrc2 in their dotfiles, and then changed the loss message to include pastebin.com/$CODE which leads you to believe that there is probably a variable called CODE included in .bashrc2
If you view the repositories in the GitHub profile, luckily, dotfiles is there!
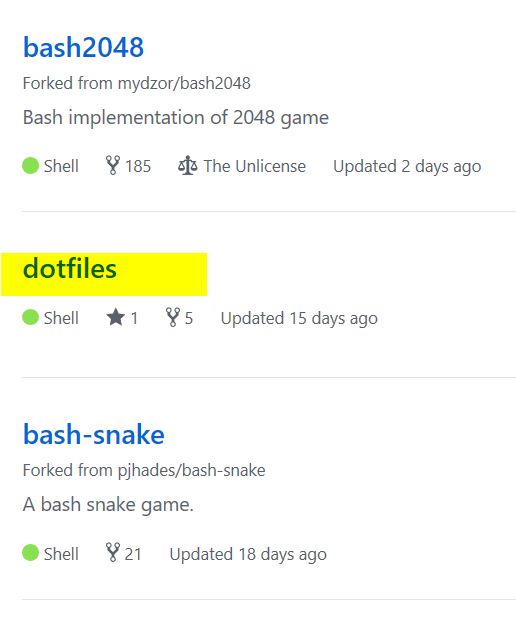
There was a fake flag placed in .bash2048, reading export FLAG="infernoCTF{}", but if you already read the bash2048 repository you would know to just look inside of .bashrc2.
On viewing the file, and using CTRL+F (or something similar) to look for CODE, you will find that it's there!
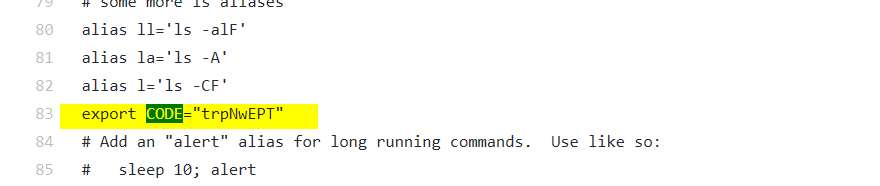
Now, you can combine this string with the pastebin link from the loss message and you will be lead to https://pastebin.com/trpNwEPT, which contains the flag.
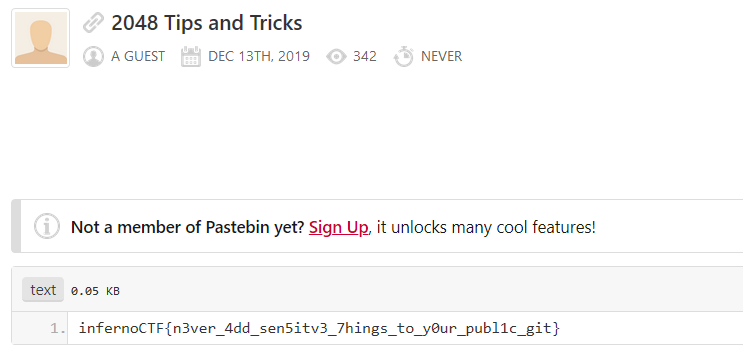
Flag: infernoCTF{n3ver_4dd_sen5itv3_7hings_to_y0ur_publ1c_git}
Although this may seem a bit “CTF-y”, the concept itself is quite realistic. I challenge the reader to attempt to find api keys or other sensitive info made public on profiles through some simple google dorking :)
Whistle Blower: Medium
After playing some 2048 you come across an interesting email exchange… What could it lead to?
employment_status.mbox
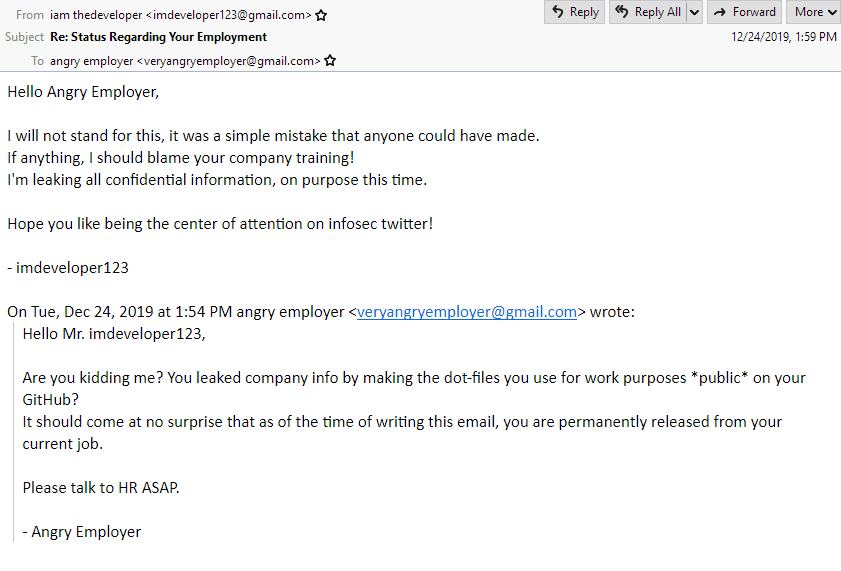
This challenge was meant to build off of the previous, with the hardest part being reading the provided emails carefully :)
If you read the reply, what should stand out to you is the following line:
Hope you like being the center of attention on infosec twitter!
In an OSINT challenge, any mention of social media should be a very clear hint towards looking for usernames, or organisations on different platforms. In this case, the name “imdeveloper123” was intentionally repeated quite a few times to get that across.
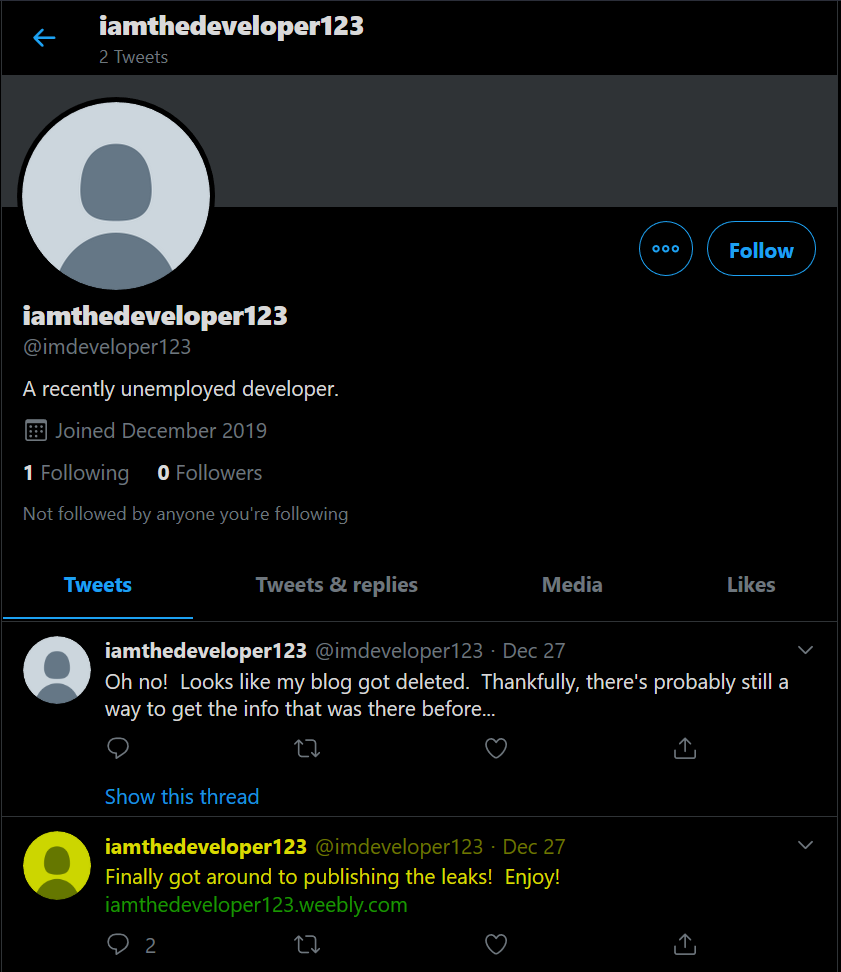
Searching for the name on twitter, you're lead to the account above, which has 2 interesting tweets; one with a link to a website which is deleted:
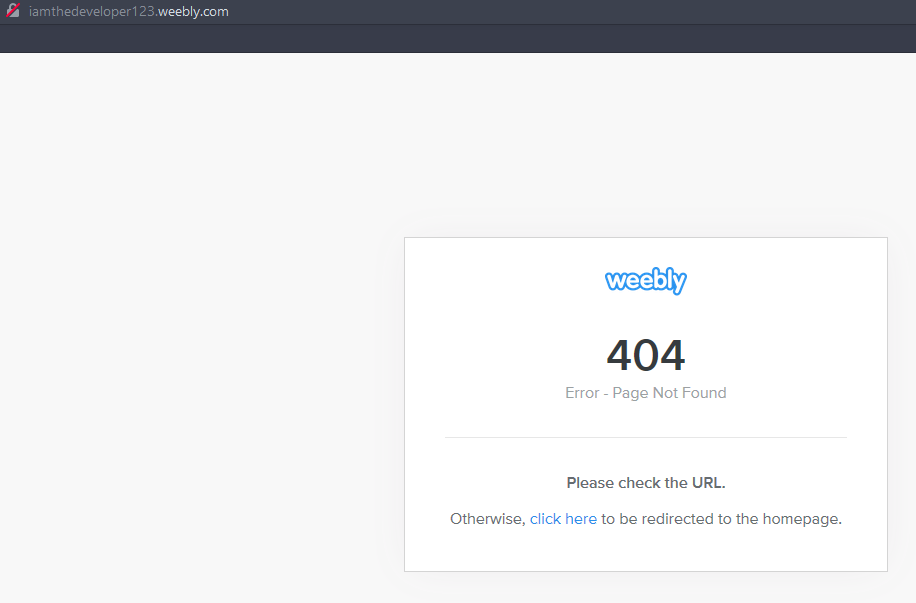
while the other tweet mentions there being a way to retrieve the content.
Fun fact: There was originally only one tweet (the first one), and the website was not deleted but had the message “THIS CONTENT WAS REMOVED BY REQUEST OF THE CONCERNED PARTY”, but… Weebly deleted the account and with it, the website. Thankfully, as you'll see when you read further, the challenge still works without the website being up, but I made the second tweet to correct for this unfortunate mishap.
At this point, you would either have been scratching your head wondering how to see what was on a deleted website, probably googling for tools, or if you're more experienced you may have gotten the right idea instantly, to go look at a web archive
In the first scenario, you could have googled: “OSINT tools for recovering lost info from website”, and the first result would have given you the answer.
Either way, you'll be led to web.archive.org and upon searching for iamthedeveloper123.weebly.com, you'll see that there was a capture taken on December 24th, giving you the flag.

Flag: infernoCTF{y0u_f0und_7h3_d1sgrun7l3d_empl0y33!}
This challenge, interestingly, only got about half the solves of New Developer (110 vs 214), and I think the reason for that was a lot of people not making it past that initial step of carefully reading through the email file given (I received a lot of dms asking for hints about the first step). This confirms what a lot of people already know, that in CTF challenges like this one, reading through all the information given to you is very important :)
Thanks for reading this far! We'll probably be hosting another CTF in the future since this one went pretty well, so follow @Dc1ph3r on twitter for any info about that.
Other Writeups:
- https://www.turkhackteam.org/capture-flag/1883541-inferno-ctf-osint-write-up-p4rs.html
- https://medium.com/@artikulouno/infernoctf-whistle-blower-ea3158894c04
- https://github.com/cnbtwriteups/Inferno_CTF_2019/blob/master/New Developer.md
- https://github.com/cnbtwriteups/Inferno_CTF_2019/blob/master/New Developer.md
- https://youtu.be/-qAUF-0px8U