
A couple weeks ago, after finding out that the Dutch Government has a vulnerability disclosure program— and that they give out tshirts for valid findings— I decided to give it a shot over the weekend.
I'll go over parts of my recon process for this program, and then how even a seemingly small bug can become potentially dangerous given the circumstance. I have been given permission to write about this, however I will be removing any references towards the name of the organization.
The scope given is any “security flaw in an ICT system belonging to central government", which is pretty huge so of course the first step is some recon.
For programs with large scopes I tend to follow my personal recon overview map, (with some modifications of course depending on the specifics on the program), and this was no different.
Note: the version of the map I have linked is currently outdated (missing a few other private and public tools). I will update it in the future.
Generally, governments will have a directory of websites they own for the benefit of citizens, so I did some google searches for this and came up with a nice list of starting points. Here are a few, you can easily find more just by looking through your search results:
- https://www.overheid.nl/english/dutch-government-websites
- https://www.oecd.org/netherlands/governmentofthenetherlandsusefullinks.htm
- https://www.ezilon.com/regional/netherlands/government/index.shtml
- https://gist.github.com/random-robbie/f985ad14fede2c04ac82dd89653f52ad
After doing some more horizontal domain association (including scraping .nl links from pages for more potential matches) I had a pretty decent amount of hosts purely from google and a bit of python+regex. Following a bit of subdomain enumeration, and looking through screenshots from my web screenshot script, I was ready to start actually looking for bugs!
Eventually I came across a subdomain that contained a small list of apps available for employees to download.
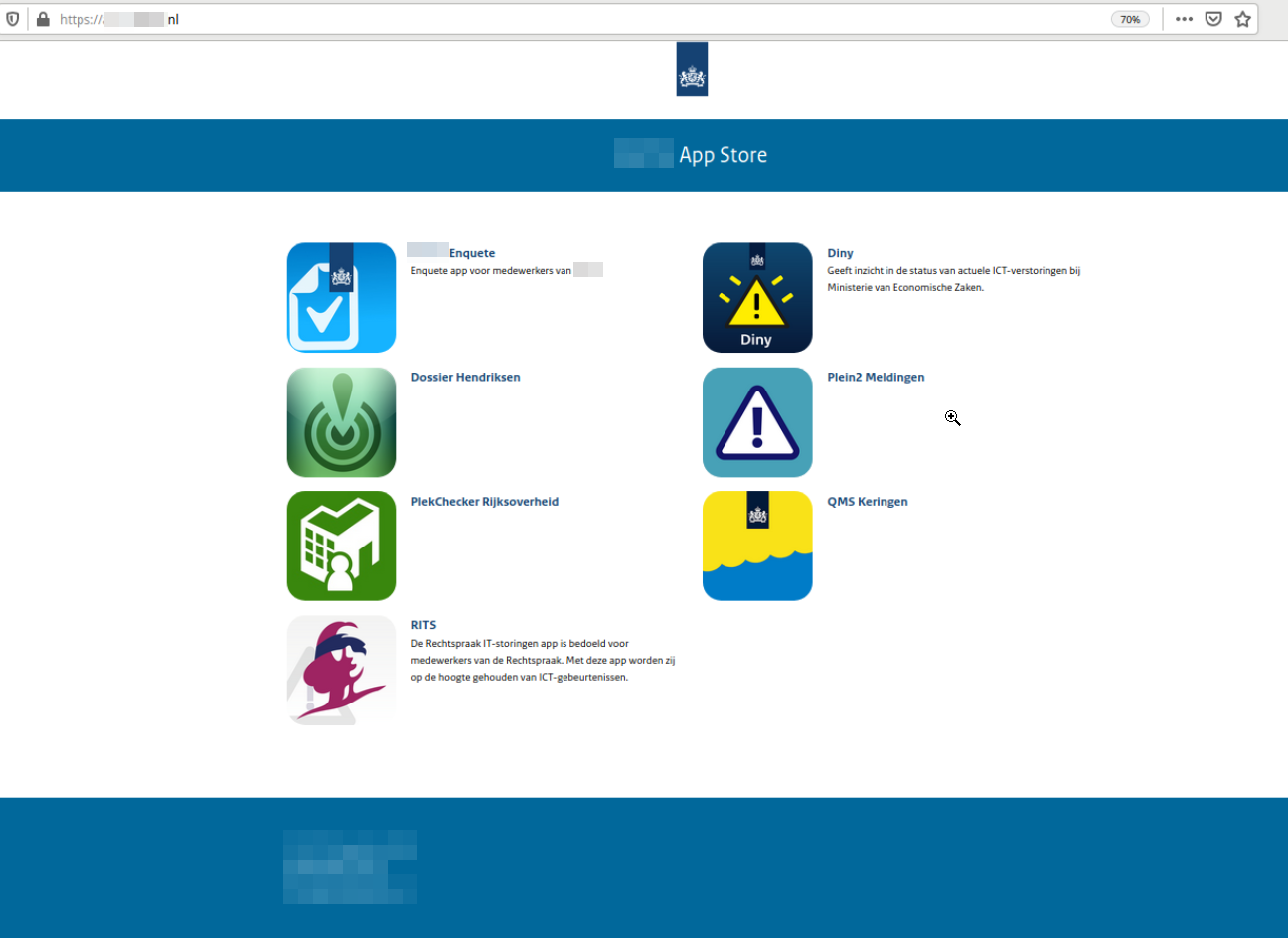
For a couple of these apps, it is required to enter an authorized email address to receive a link to download (most notably, the IT Disruptions app in the bottom left of the above image). If the email you enter is invalid, you will be met with an error:
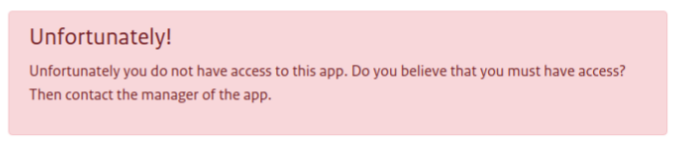
I then tried the email user@subdomain.redacted.nl to attempt to see which emails were accepted, and the response contained a success message. The link was sent to the email I had entered.
(I'm sure many CTF players can see where this is going :P)
Next, I tested to see if the validation was checking for if the domain needed to be at the end, or just present in the email. I set up a test mail account on my domain that contained the Netherlands domain as a subdomain, and then one that had the Netherlands domain inside of the username.
And… Both worked!
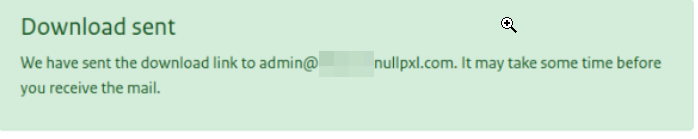
From this we can see that the backend is simply checking for the string redacted.nl inside of the provided email, and not if the email itself meets the requirements.
I checked my inbox and sure enough I had received a link and QR code to download the app.
Although this bug is quite small, It doesn't take a lot of imagination to picture what a an attacker may be able to do with the ability to view IT events intended for the employees of the Judiciary. My point being: the place a bug exists is often more important than the bug itself. An RCE on a basically meaningless system disconnected from anything of value may be less impactful than a reflected XSS on an extremely critical domain.
Only a couple days after the issue was reported, it was fixed and I was offered the t-shirt I wanted from the start :P
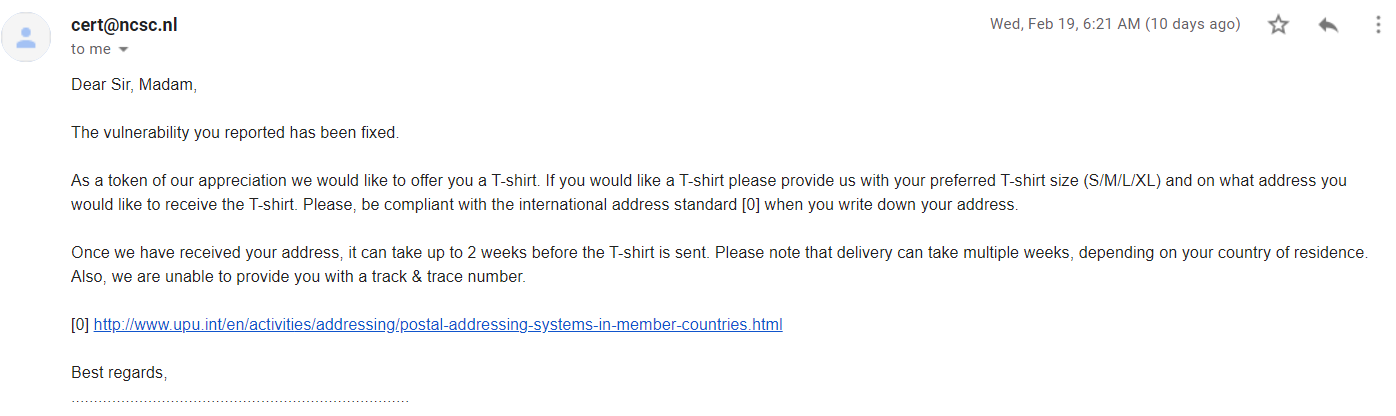
Great speed from the Dutch Government to resolve the issue, and I would recommend their program to anyone wishing to practice some recon on a large scope.
